Ooops, your day may have been ruined!
Introduction
Well, I don’t think this one needs a lot of introduction because the chances that you haven’t heard about this latest ransomware problem are pretty slim.
So, assuming we all know what it is and what ransomware does, how many people have observed the process in detail?
Sounds like it’s time to take a closer look at what actually happens when a system gets infected.
(Don’t forget to click the screenshots if you want to read the details)
How the test was performed.
In this scenario, I created a Windows 10 Virtual Machine, planted a few decoy files and installed some common applications like Microsoft Office 2016, Mozilla Firefox and 7Zip.
Now, of course we aren’t going to infect this machine and just shut it down again, we want to monitor it and have a way to reclaim control over the VM. To achieve this I used the next-gen AV solution SentinelOne.
SentinelOne is different than regular AV solutions because it does not only look at the hash of the malware files, but instead looks at what it does.
I won’t go into the technical details, perhaps in a future blogpost, so to keep it short: Imagine opening a Word file and the second you do that, it starts creating new processes, modifies registry entries, etc. SentinelOne monitors this behavior and when a certain threshold of suspicious behavior is reached it kills the process and rolls back the changes made by the malware.
Results: What happens when you execute the malware?
I executed the WannaCry ransomware on the VM and configured SentinelOne to only alert instead of killing the process. SentinelOne keeps monitoring the VM and auto-creates a nifty report in the management console.
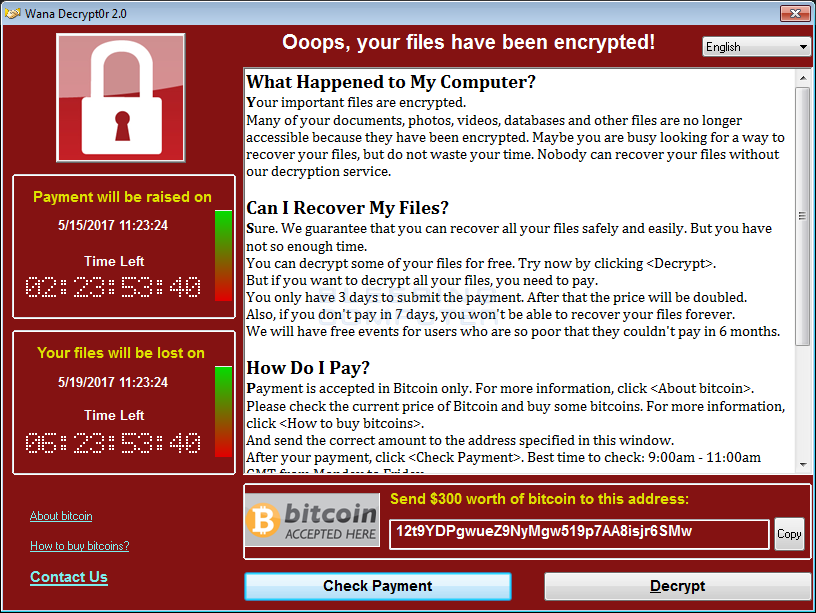
Keep in mind that at this point, the entire VM has been encrypted and these nice people are offering me the decryption key for bitcoins.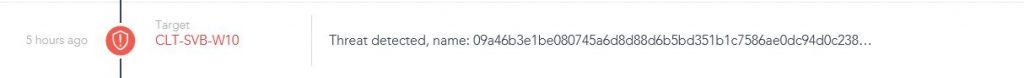
So, this entire process resulted in a .CSV report featuring a small amount of… 17288 rows! I selected a few interesting parts to highlight in this post, let’s start by taking a look at who this bad boy tries to talk to.
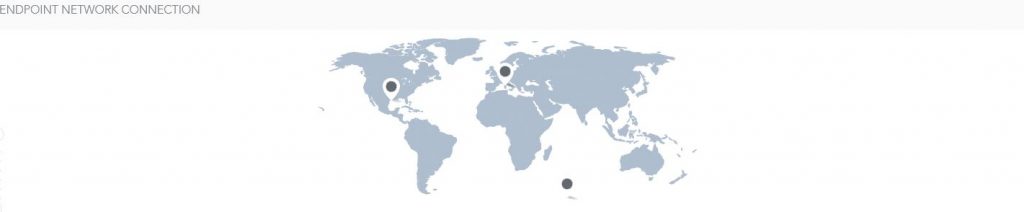
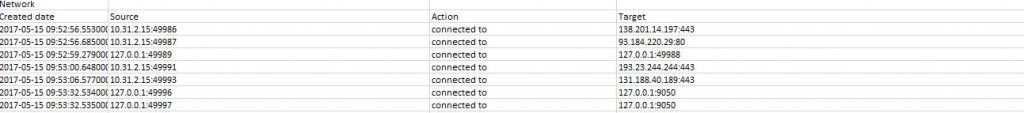 Friends in Germany and the USA, so no Russian/North-Korean/Chinese/Mordor influence so far.
Friends in Germany and the USA, so no Russian/North-Korean/Chinese/Mordor influence so far.
Onwards to the ‘installation’ of the ransomware, the creators took their time to provide proper customer service and included translations for 28(!) languages to show the payment instructions in:
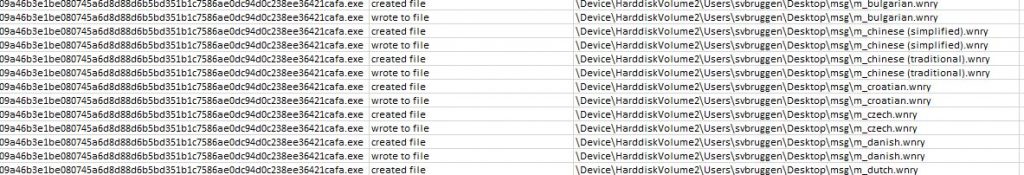
Next, it downloads the readme-file, the background.jpg to replace the users wallpaper with, the decryptor-tool to fill in the key with after payment, and multiple .bin.gz files.
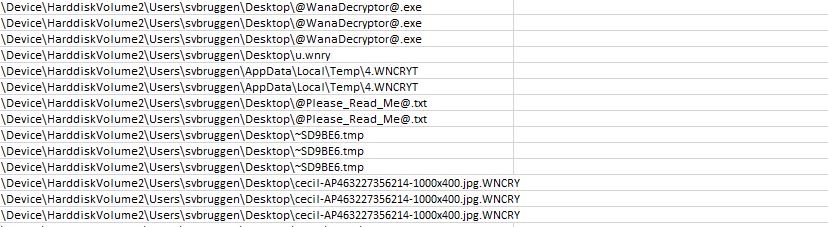
Not visible in this screenshot but interesting nevertheless, it even downloads a TOR browser for you! How nice of them.
Of course, the process would not be complete without deleting shadow copies, stopping services and acquiring persistence on the machine: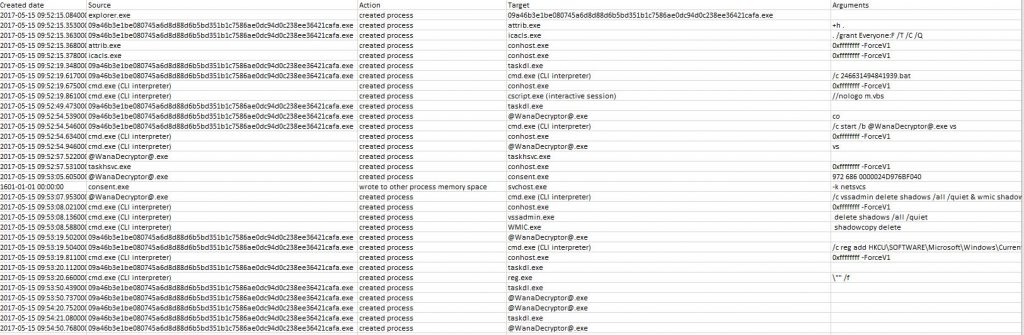
And now it starts wreaking havoc, in a time-span of barely two minutes (you read that correct, two. minutes.) it encrypts everything it can find on the machine rendering it completely out of order until the ransom is paid.
Conclusion.
Because SentinelOne is running on the machine, getting rid of the infection was quite simple by issuing a Rollback-command from the management console.
By using this option, SentinelOne rolls back all the changes made by the ransomware and notifies the user that the system has to be rebooted.
After the reboot, the machine is back in it’s original pre-infected state and the infected files are cleaned up.
Of course, in a production environment you would configure SentinelOne to kill the process right away to prevent further damage. You also have the option to disconnect the machine’s network connection and notify the other clients about the infection’s behavior so that they can prevent getting infected themselves as an auto-immune response.
If you are interested in the report containing the raw data, contact me on Twitter (@SvanBr) or shoot me an E-mail.
Disclaimer: I am not sponsored by SentinelOne in any way.






